The infrastructure, the users, and the services offered on computer networks today are all subject to a wide variety of risks posed by threats that include distributed denial of service attacks, intrusions of various kinds, eavesdropping, hacking, phishing, worms, viruses, spams, etc. In order to counter the risk posed by these threats, network users have traditionally resorted to antivirus and anti-spam software, firewalls, intrusion-detection systems (IDSs), and other add-ons to reduce the likelihood of being affected by threats. In practice, a large industry (companies like Symantec, McAfee, etc.) as well as considerable research efforts are currently centered around developing and deploying tools and techniques to detect threats and anomalies in order to protect the cyber infrastructure and its users from the resulting negative impact of the anomalies.
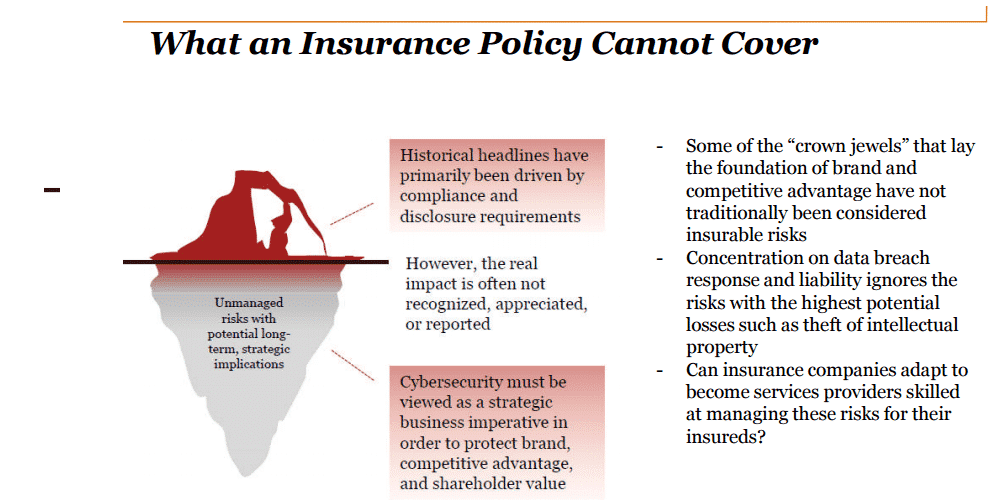
In spite of improvements in risk protection techniques over the last decade due to hardware, software and cryptographic methodologies, it is impossible to achieve perfect/near-perfect cyber-security protection.
As of 2014, 90% of the cyber-insurance premium volume was covering exposure in the United States. Although at least 50 insurance companies have cyber-insurance product offerings, the actual writing is concentrated within a group of five underwriters.
Many insurance companies have been hesitant to enter this coverage market, as sound actuarial data for the cyber exposure is non-existent. Hampering the development of this actuarial data is inadequate disclosure regarding cyber attacks by those affected.
With cyber insurance premiums expected to grow from around $2 billion in 2015 to an estimated $20 billion or more by 2025, insurers and reinsurers are continuing to refine underwriting requirements. Market immaturity and lack of standardization are two reasons why underwriting cyber products today make it an interesting place to be in the insurance world. Not only do you have an insurance marketplace that’s trying to reach a standard and accommodate the needs of today’s insured, but you also, at the same time, have a rapidly developing exposure landscape and capacity available.
Obviously, the quoted line explains the situation why it is hard to have products in this field. We neither have such model nor the data that eventually is hidden from being exposed because of goodwill of the company. Definitely I’m looking for some miracle to happen in near time for Cyber Insurance products. Covering more in upcoming articles.
PS: Going through Mr. ROBOT and finally after more than an year to revive the draft of cyber insurance from my drafts, finally felt that this is important!
What do you think? Can the outcomes of an attack be shared with Actuaries or any hidden Actuarial Society (Not CIA, please)? Thoughts in the comments
